Why Businesses Today are Choosing Managed IT Services
Published in Technology
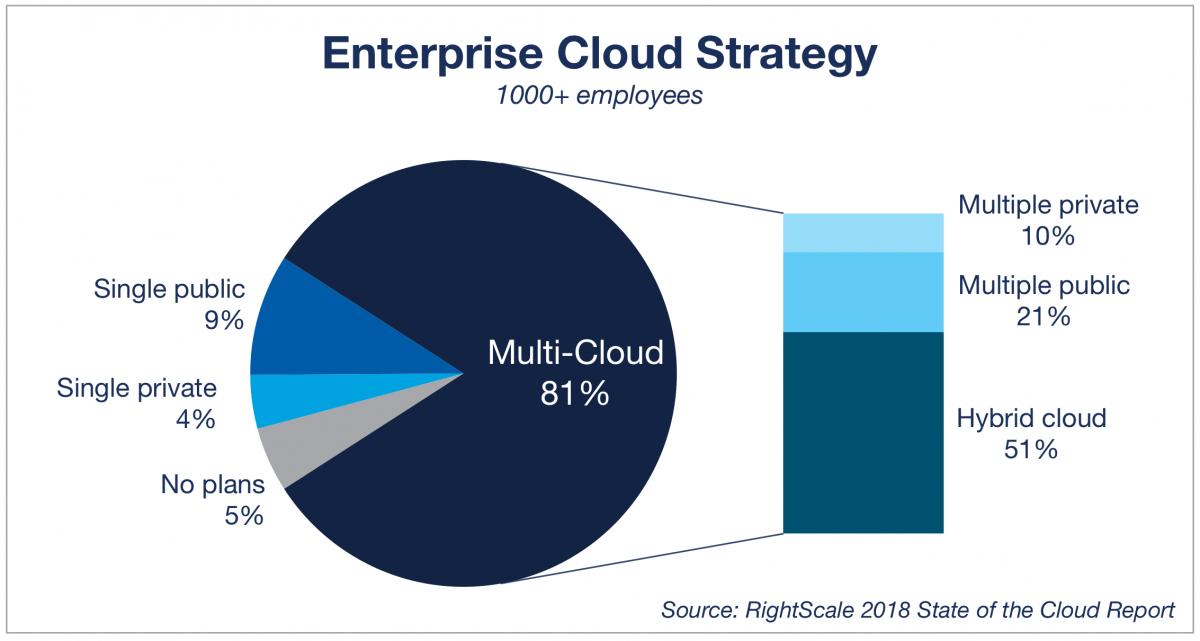
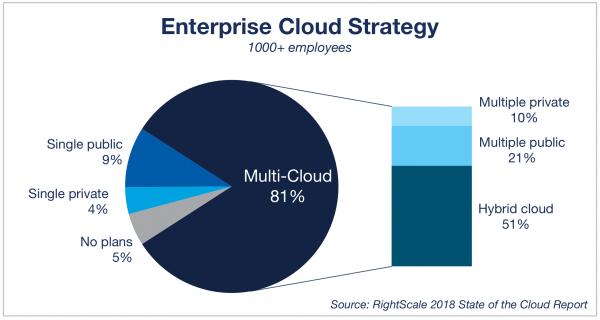
Staggering statistics were published stating that by 2019, the managed-services market is expected to see growth by as much as $193 billion . What is it about this particular business model that is so wildly successful? It seems a large percentage of small- and medium-sized businesses are very much in favor of these services, and there are a number of good reasons why.
Why the Demand for Managed Services?
We have already established that business owners are drawn to the managed-services business model, but why? What is it that owners are hoping to get out of such services, and how can you use those wants to market your services? Research shows that the reason our clients choose our services are not necessarily the reasons why we think they should. Business owners are looking for a wide range of benefits when they opt for a managed services model, and what they want is:
- To improve the efficiency and dependability of their IT operations.
- Enhanced security and compliance.
- A proactive approach to maintenance.
- Cost effectiveness and a good return on investment.
- Free up IT staff to work on strategic projects.
- Have greater access to new technologies.
- Lacks in-house IT capabilities for certain functions.
- Shifting capital expenses to operating expenses.
- Predictable pricing and manageable costs.
Let’s take a closer look at some of the more pressing reasons why managed services are becoming the obvious choice for small to medium sized business owners.
- More Efficient and Reliable IT Operations
This is one of the main reasons that companies with over 100 employees decide that managed services are the right choice for them. Often, the businesses we partner with as managed-service providers are suffering from overburdened IT staff, or lack employees that have the knowledge and skills to handle certain tasks and successfully handle the entire network on their own.
In these situations, it is hard to deny the value of working with an outside IT service provider. A majority of businesses using managed-services describe their partnership with their provider as a collaborative arrangement with their internal IT department, leading one to believe that certain aspects of IT management fall into the MSP bucket while others are preferably handled in-house. The driving force for these business owners is to improve and enhance the capabilities of the in-house IT team, not replace them altogether. Outsourcing IT not only ensures an extra team of IT experts to help resolve any issues or concerns but to be able to benefit from having access to the latest and greatest technology and innovative business grade solutions that will assist in maximizing uptime and profitability. These technologies include such things as:
- Remote monitoring and management (RMM)
- Backup and disaster recovery (BDR)
- Cloud computing
By investing in these tools the entire IT infrastructure becomes more reliable and dependable, labor constraints are overcome, and internal IT departments are able to keep in control of the situation.
- Enhanced Security and Compliance
There are so many variations of technology that store and transmit data nowadays, including tablets, operating systems, servers, smartphones, laptops and more. Because data is stored and transmitted on these devices it means their security is critical. Many business owners live in fear that they will fall victim to a security breach. As a managed service provider it is your job to make them well aware of the risks, sharing examples that have been highlighted in the media and explaining how their data and compliance practices are compromised when such an event arises.
It is also crucial you address the business owners concerns about compliance, especially in industries such as health and legal, where compliance is a major concern. For these people it is important they work with a provider that is HIPAA compliant and in addition, can implement other ways to supplement additional managed security protocol, policies, and procedures.
- A Proactive Approach to Maintenance
This is a major and important benefit to managed IT services. Business owners have little to no time to spend thinking about their IT infrastructure, worrying about things such as the dependability and speed of the network connections, and other concerns. By working with an MSP they are afforded the luxury of all-day, every-day, around-the-clock coverage.
Security solutions and services such as RMM are always working to detect potential threats, vulnerabilities, or potential disturbances. When you provide fully managed IT support, bugs and issues can most often be troubleshot and remediated before they are ever a concern to the business owner. Owners are happy to pay for such a service, as CEOs and others have no time to be verifying that backups are done properly. It has become more than clear that data management on the cloud is expected to yield more managed services revenue in the coming year, and when business work with the right MSP they are able to take advantage of proactive business continuity solutions, such as BDR, by combining RMM intelligence with regular and encrypted backups, cloud computing, and virtualization.
- Cost Effectiveness and Return on Investment
The cost savings associated with managed services is considerable, making it another reason that using MSP’s is desirable. This fact has an incredible amount of business value, but many business owners are unaware of just how significant this is. It is your job as a managed service provider to explain to your clients how MSPs help control outgoing expenses and increase ROI. An IT budget consists of many items, including:
- Hardware costs
- Software and network infrastructure
- Maintenance costs
- IT labor
The businesses you work with need to understand every-way that managed services can benefit them financially, especially where the aforementioned maintenance costs are concerned. Using outdated software can have detrimental effects on ROI, and this is avoided with MSPs. In additional it provides the flexibility and scalability needed to grow or scale back in a way not possible with internal IT teams.
The managed service model allows clients to easily predict their IT expenses on a monthly basis and are able to better plan and budget for larger IT projects and improvements. All of these factors should be reviewed in a quarterly business review. You are able to show your clients the value of your services during these reviews, and how you play an instrumental role in what they do.
- Free Up Internal IT Staff To Work On Strategic Projects
When businesses choose a managed-service provider a major advantage they often don’t think of with an outside service provider, is that any internal IT staff is free to focus their energy and talents on projects and tasks they are better suited to handle.
This increases productivity and allows strategic planning to get the time and attention it deserves.
This maximizes the business’s IT budget and the business is able to get the most out of their investment.
It doesn’t make much sense to have your internal IT team handling things they have little expertise or experience with. Things like migrating over to Microsoft Office 365 when it can be expertly handled by an MSP instead, and the technician can commit their time to something they excel at. Managed-services enable in-house staff to spend their working hours on what they are best at, with the MSP filling in the gaps and taking the pressure off, providing specialized services where they are needed most.
As managed service providers Aphelion is well aware of the benefits and advantages of the services we offer, but it is our job to help our clients see them as well. By better understanding what it is they are looking for and how their businesses can be best supported we are able to tailor our offerings and approach to better meet those needs.
Want to talk more about the advantages of managed services? Contact us